What is Workforce Enablement?
Definition of IT Workforce Enablement? Your company may boost employee and customer satisfation by utilizing cutting-edge technology and data. Customer requirements shift, as they usually do, and it’s not a surprise. About IT Workforce Enablement: What do we know? We know that our customers are always on the go and work on tools in their […]
What is Agile?
Agile Definition ? Agile is defined as the capacity to respond to change and the skill to create. It has everything to do with the thought process that occurs during risk management. This software sets values that allow businesses to be more adaptable. The concept of Agile was introduced in software development to solve heavily […]
What is ITSM? Everything To Know About IT Service Management
What is ITSM? IT service management (also known as ITSM) is the art of planning, executing, and providing IT services to satisfy an organization’s needs. It guarantees that the right people, procedures, and technology are in place to deliver results. About ITSM If change management ITSM is the art of running a business, it raises […]
What is ITIL? Your guide to the IT Infrastructure Library
About ITIL One of the most popular IT Service Management frameworks in the world, the IT Infrastructure Library (ITIL) provides an organization with the focus necessary and its employees a road map to ITIL change management, besides providing the makeover and maturity. With it, efficiency can be enhanced and successful service levels can be attained. […]
What is Incident Management ?
When important equipment of an organization is down, affecting its productivity drastically, it is an incident. What incident management does is address such situations effectively so that the affected party is back in business again. There are other kinds of sticky situations firms can find themselves in, and these IT disruptions can harm their operations […]
What is IT Change Management?
A procedure of IT Service Management, the aim of IT Change Management is to make things simpler for an organization to introduce alteration requests to its IT ecosystem. By using it, an organization can request, rank, sanction, allow, plan and deploy conversions anywhere in its infrastructure. A capable IT Change Management method can help companies […]
The Configuration Management Database Services | MIRAT
Overview The Configuration Management Database or the CMDB definition goes something like this: it is used to keep track of the state of assets like products, systems, software, facilities used in the company’s IT services, and the connection between those components. Wondering what is CMDB? It works for a specific view of configuration data and […]
MIRAT | Suits Your IT Asset Discovery Needs
Overview Wondering what IT asset discovery is? For the last several years, companies are moving towards an IT diversified environment that includes cloud, virtual, and mobile devices. The companies decided to make a commonplace for connecting or disconnecting the enterprise network. All these developments put a challenge in front of them to maintain and control […]
Experience MIRAT Self-Healing Tool
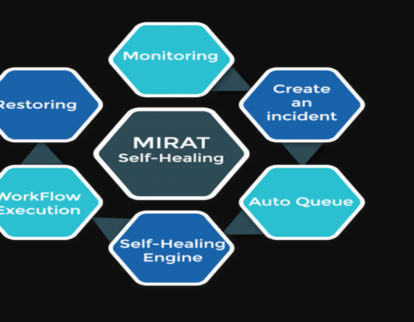
Overview In Self-healing process, the system ability to detect and resolve problems instantly and automatically. It just prevents human intervention to fix issues. The technology of self- healing is better fitted in IT Infrastructure to fix problems faster than human as it reacts immediately based on rules and machine learning. You can scale a self-healing environment without […]
MIRAT – The Best Vulnerability Management Tool
Overview In vulnerability management there is a continual process of testing, reporting, response, and triage. The security of the assets is an ongoing process. Security is mostly applicable in vulnerability assessments. In day-to-day work, most companies think about susceptibility. The security is mainly changing based on your network and IT infrastructure. From time to time, […]